VoIP systems are becoming popular among businesses, and this trend is only expected to grow over time.
The growth of VoIP solutions also means that more businesses are becoming targets for malicious attacks. This gives rise to the most common question- Is the VoIP secure?
In spite of the many benefits, security remains a major concern among VoIP users. A recent report from The Irish Times claimed that phone, email, and text scams have increased by 80%, and more than €640,000 has been stolen through phishing, vishing, and smishing crimes in 2020.
These attacks can result in loss of critical information, loss of revenues and client information, hardware damage, and more.
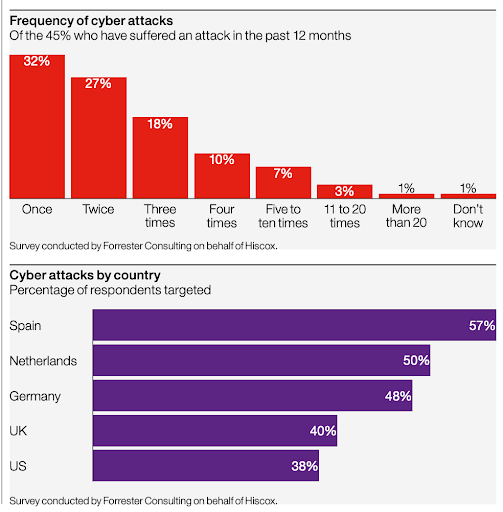
Source: Hiscox
In order to help businesses protect themselves against these attacks and to be aware of the risks associated with VoIP, here is a VoIP security audit Checklist:
VoIP Security Audit Checklist:
It is easy to find the most appropriate solution to save a business when you are aware of the potential threats.
In case you are currently researching for a reliable VoIP system or have installed one, you might be struggling with a few questions, generally from these three aspects:
✅ The Top VoIP security risks
✅ Best practices to secure a VoIP system
✅ Top 5+ Things To look When Having a VoIP Service Provider
Let’s dive into the answers to these VoIP security checklist questions;
✅ The Top VOIP Security Risks:
Softphones, Smart devices, IP desk phones all possess potential risks for the best VOIP security systems. Some of the common ones are:
- Network Firewall
- DDoS (Distributed Denial of Service) Attack
- Call Tempering
- Vishing
- SPIT
Network Firewalls:
Despite the fact that hardware and software firewalls are designed to protect your system, some don’t offer this feature. Old firewalls don’t recognize VOIP service, so they block the VoIP protocols and also take a lot of time to scan the information.
Ensure that your system has an updated firewall to protect your system from sudden slowdowns and poor performances.
DDoS Attack:
A distributed denial-of-service attack is a malicious attempt to hinder the normal data traffic of an internet server, service, or network by increasing Internet traffic.
In simple terms, it is like an unexpected roadblock where some protestors have jammed the road, and are not letting vehicles reach their destination.
How will you identify a DDoS attack?
The most obvious symptom of such an attack is that the service or the website suddenly stops working or becomes slow. You may notice performance issues, a suspicious amount of traffic coming from a single IP range, strange traffic patterns like a spike at odd hours, lots of traffic coming from the same geographic location or web browser, etc.
Call Tempering:
Call tempering is a hacking attack where the hacker is attempting to harm your call quality. This is done by disrupting the audio signals with delay or call silence. Attackers send the interrupted data packet along with the calls, causing a packet loss of the original VoIP calls.
Vishing:
Blank calls or calls where there is no response are considered vishing attacks! Vishing, the combination of voice + phishing, is a phone-based attack that aims to get you to reveal your personal information.
During this attack, the hacker uses social engineering to get financial, personal, and other important details about your business. So, be cautious when you hear things like ‘We are calling from XX bank,’ ‘your account has been attacked,’ or anything. These callers may offer assistance installing software or ask for software updates.
SPIT:
Spam Over Internet Technology is an automated, undesired and prerecorded, bulk telephone call made through a hosted VoIP phone service. This is email spam that sends a prerecorded message to the VoIP phone system.
✅ 7 Best Practices to Secure a VoIP System
VoIP is a system that leads to a high level of security risk for businesses that handle personal information over the phone.
Whether a client is sharing a social security number or bank account details, their credentials should be kept secure and encrypted.
Here are seven ways you can secure your business VoIP system and protect sensitive data:
- Strengthen your passwords
- Don’t use the Phone Web Interface
- Enable Wi-Fi encryption
- Block private calls and restrict international calls
- Report Ghost Calls
- Recruit network managers
- Set geo-restrictions
Let’s understand exactly how! (Don’t Miss the Bonus Tip at the End)
1. Strengthen your passwords
More and more cases of data breaches and malicious attacks are emerging, with 40% of accounts on the Internet being hacked using just a password. The password can be protected somewhat on personal phones, but on VoIP business phones, just a Google search can enable hackers to hack into the system and steal the password.
It’s no secret that we should have strong passwords, but a surprising number of people still use their business name, brand name, 1234, or simply ‘passwords’ as their passwords. Another most common mistake is having generic or the same passwords for multiple systems. This is something you should avoid!
To strengthen your password, mix uppercase, lowercase, numeric, and special characters. Enable two-factor authentication and make it mandatory for all your employees who use the VoIP phone system.
Security experts recommend changing passwords frequently, at least once a month.
2. Deactivate Phone Web Interface
VoIP phone’s web interface lets you manage business-hosted VoIP accounts, call settings, SIP settings, and other important features. You can view passwords and usernames in plain text (using the backup configuration of the phone), making the web interface the most vulnerable point of attack.
Hackers do not need to be on a LAN to access VoIP’s web interface. They can do it using the open internet by just having the phone’s private IP address.
Therefore, you should turn off your phone’s web interface to prevent hackers from accessing your phone’s backup configurations.
You can re-enable it anytime when needed; you just have to consult support for detailed instructions on enabling and disabling the web interface.
3. Wi-Fi Encryption
Activate WPA2 on wireless networks and train your employees about the same. Ask them to use encryption when they use Wi-Fi networks. Experts advise businesses to update their Wi-Fi passwords every year to ensure their safety and security.
There are two types of encryption for Wi-Fi, WEP and WPA, i.e., Wired Equivalent Privacy and Wi-Fi Protected Access. All you have to do is choose a WPA2 router that is compatible with your devices.
4. Block Private Calls, Restrict International Calls
Hackers use business VoIP phones to rack up calling minutes for international phone numbers. The risk is higher during holidays, off business hours, and long weekends; you might notice a long-overdue bill when you come back.
So, if your business doesn’t require international calls in daily operation, disable them! Calling cards are available for purchase if you need to make international calls frequently. It is important that you keep an eye on your phone records and check the CDR (call detail record) if you need to turn on international calling.
5. Report Ghost Calls
It is highly recommended to instruct your staff to report ghost calls when maintaining VoIP security. No matter how many voicemails go unreceived or how many ghost calls you to get, you should always report them. The staff must be trained not to keep voice messages longer than needed.
Hence, reporting is the only way to get rid of ghost calls, unwanted calls, and lost voice calls.
6. Hire Network Managers:
VoIP business networks require constant monitoring to maintain call quality. You need to identify the QoS metrics of your network and test various management tools to ensure everything is working properly. While small businesses can use trusted network management software to do this, some require dedicated IT staff to set up VoIP at the customer help desk and in other areas of the business.
7. Set Geo Limits:
Setting geo limits reduces the risk of infiltration and protects your VoIP system. By doing this, you restrict the use of VoIP phone systems to restrained geographic locations. This will prevent remote hackers from accessing your system.
✅ 5+ Things to Look for When Choosing a Secure VoIP Provider
Since VoIP comes with a wide range of prices, services, and features, choosing the best service provider from an array of providers can be overwhelming.
Here are a few tips for choosing a VoIP service provider for your business:
VoIP Equipment Type:
Some VoIP services use the Internet for making inbound and outbound calls, while others require you to invest in specific equipment. Many companies opt for hosted VoIP solutions, where the provider installs all hardware and software.
Therefore, identify your type, and then install the services because this configuration can save you a significant amount of money.
Cost:
Hosted VoIP is less expensive than on-premises VoIP, but there are still many cost options. So, it will be a smart thing to compare features before choosing one. Additionally, it is a good idea to set a budget before you begin comparing.
Keep in mind these factors before you start comparing:
- Cost of features and upgrades
- Commitments related to cost in the contract
- The cost of IP phones
- Training and Support Cost
- Set up fee
- Any upfront fee
Flexibility:
How difficult is it to customize your system and make technical changes? Maybe you need a technician! So, if flexibility is what you want, make sure you choose a VoIP solutions provider who has a dedicated online portal or app where you can easily make changes.
This way, you will be in control of everything and can change according to your business needs.
Features:
Most VoIP service providers offer standard features like conference calling, Voicemail-to-email, analytics, automatic call distribution, auto-attendant, call recording, hold music, and a lot without paying extra. However, you must ask which features, and in the package and which will cost you extra.
Security:
When choosing a hosted VoIP solution, you have full control over the security, which can be scary for businesses whose main concern is keeping information confidential. Ask everything you can about security protocols and how the service providers encrypt data. You will have peace of mind knowing that your client’s information is safe.
Training/Onboarding:
Getting used to anything new can be challenging. Ask your service provider if they provide any training manual, documentation, video, or any complementary training to make your team familiar with new things. Also, find out if the training is on-site or remote; depending upon the size of your business, you might choose one over the other.
Contracts and Commitments:
No matter how impressive and promising a service provider seems, you never know what can happen next? They might cancel the service, or you decide to choose someone over them.
If you get bound by a contract, you might end up with something you don’t like or get fined some dollars if you break the contract. Choose a provider who offers contract-free service.
Also, here’s the bonus tip that we promised to share with you:
|
Conclusion:
VoIP security is essential to protect critical information about your business. So, let this checklist be your guide to a better VoIP system to help you prevent phone frauds without compromising your security.
Some more tips to follow before you go:
- Delete/Change passwords for the ex-employees of your business
- Protect your VoIP system by restricting access.
- Fully understand the capabilities & functionalities of the system yourself
- Block access to unallocated mailboxes
- Restrict out of hours calls
- Enable authentication for all user accounts using strong passwords.



